
The investigation into the culprit behind the WannaCry ransomware attack is ongoing, according to a Department of Homeland Security official.
On May 12, WannaCry ransomware infected hundreds of thousands of computers in more than 150 countries. The ransomware targeted computers running on dated Windows operating systems.
According to the DHS official, who spoke exclusively to MeriTalk on the provision of anonymity, the agency sprang into action as soon as the U.S. Computer Emergency Readiness Team posted reports. DHS ran a detection probe to scan for the software after the reports were issued.
“What’s most important here is that WannaCry is one shade of gray of the ransomware we’ve seen over the past year,” the DHS official said.
DHS’s operations center posted bulletins containing information on WannaCry for other agencies’ reference soon after the attack, the official said.
DHS is tasked with supporting the FBI, which is in charge of the investigation into who is responsible for these attacks. These investigations can take a long time, as they require pinpointing the geographic epicenter of the attack as well as identifying the person or group behind it.
“We’ll keep pushing out information as we get it,” the DHS official said.
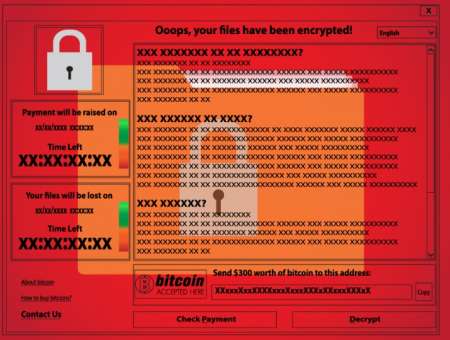
Although WannaCry paralyzed computers in many countries, Federal systems emerged from the attack unscathed. According to the DHS official, these systems remained unharmed because the vast majority of Federal agencies use newer models of Windows operating systems. DHS and the Office of Management and Budget mandated that all agencies update from Windows XP by 2014.
“There are very, very few agencies deploying Windows XP in any number,” the official said. “It hasn’t been supported in three years.”
The WannaCry attack is one of several cyber incidents over the past few years, and DHS has been releasing tools for agencies to manage cyber risk and keep pace with these attacks. One such tool is the Continuous Diagnostics and Mitigation program. Mandated by OMB in 2012, CDM provides Federal agencies with tools to identify and address cyber threats.
The DHS official stated that six agencies currently employ CDM to detect vulnerabilities in their systems.
“It’ll be easier and easier and faster and faster for agencies to identify vulnerabilities,” the DHS official said.
Another resource is the Einstein program, which blocks cyberattacks from plaguing Federal agencies and also provides DHS with a way to glean information about attacks and create defenses for addressing similar ones.
While the Einstein program was created in 2003, it has evolved over the years. The DHS official said that the ultimate goal of the next phase of the Einstein program is to identify a threat the agency has not seen before.
“This will let us be more agile in blocking threats before they enter Federal systems,” the DHS official said.
