Editor’s Note: The following story is taken from a book-length work authored by a senior Federal IT official currently working in government. This is one part of an extensive, firsthand account of how IT decisions are made, the obstacles standing in the way of real change in government technology management, and what one career Federal IT employee really thinks about the way government does IT.
Because the author is a current government employee and is concerned about the impact this may have on their career, we’ve agreed to publish this series of weekly excerpts under the author’s chosen pseudonym—Demosthenes.
MeriTalk has agreed not to make substantive changes to any of the chapters.
— Dan Verton, Executive Editor
Security
I have already talked a little about security. From a development perspective we need to bake security into the project from day 1, not wait until the end to perform testing. Also, I mentioned that part of the quality management should include a source code scanning capability to detect common vulnerabilities early in the development process.
CDM
When it comes to the broader discussion of protecting the enterprise, the Continuous Diagnostic and Mitigation program (CDM) is a good first step. There is a reason why I put CDM chapter immediately after Commodity IT. CDM is part commodity and part security. It is partly focused on addressing the fragmentation of agency buying on this category of stuff. But it is also partly focused in getting families of products that work well together.
I will start out by giving you the bottom line up front. The biggest knock on CDM is that it was dominated by the same companies that have dominated the government’s IT business for the last 20 years (above right). The issue is that there is no new thinking here, there is a lot of the same old profiteering thinking.
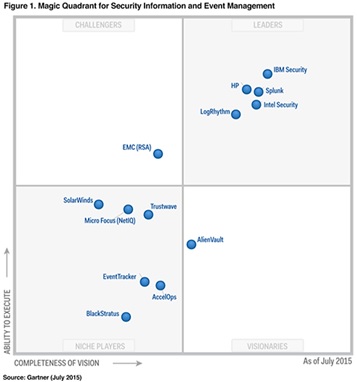
What do we think of this list? I’m not saying it is terrible, but I am saying I have heard that song before. Above is the Gartner Magic Quadrant for Security Information and Event Management, a lot of what CDM is intending to deliver. I might be crazy, but IBM and HP are in the CDM list. But no other company in the magic quadrant analysis is an offeror under CDM. That should communicate something about CDM shouldn’t it? That only two of the leading companies in a field are prime contract holders for one of the most important contracts to get our cybersecurity house in order.
Where are Splunk, LogRhythm, Intel Security, and the other firms? Are there barriers to entry in the Federal space? Who is creating these barriers and why? I think that for CDM to continue to be effective in both securing agencies’ IT environments and efficiently managing the spending in this space, CDM must continue to evolve, and that means bringing in some new blood. We need some companies that are willing to challenge conventional thinking and bring new ideas and techniques to the table.
Remember, Enterprise Architecture was a false first step and we spent a lot of money and wasted a lot of time because industry told us that was the way to go. I worry that we are once again planting the seeds of that painful lesson by not including more disruptive companies in CDM. Thus one big thing to consider is how we can on-ramp some new entrants into CDM and incorporate some disruptive competition that may change the game.
CDM was broken down into three phases. The first phase was focused on getting the tools to perform asset management. This initial step was really important because CIOs needs to know what they have in their enterprise both from a hardware perspective as well as software. I dwelled on this point in the last chapter about Commodity IT. These asset management tools must be used to support both the security activities as well as the acquisition activities of the agencies. If your agency has 100,000 Dell laptops, you need to use this set of tools to know which ones have which hardware vulnerabilities and which ones need to be replaced this year versus next year and beyond.
The second phase of CDM was focused on getting the professional services to calibrate the tools and to get them to deliver the right information at the right time. Luke McCormack, the CIO at DHS, often used a good analogy to describe this process. He said that when you get the tools and install them, everything in the organization will light up like a Christmas tree. If you think about thousands of lights illuminating at the same time, it is nearly impossible to figure out the five or six that are really important that you have to pay attention to right now. Thus if everything is a priority, nothing is a priority. That’s why we need the services to tune these tools so that the truly important information rises to the top and we dedicate resources to those limited things.
The third and final phase of CDM is intended to deliver a dashboard. As I write this, that part is still under agency-sponsored corrective action following the protest from one or more of the losers. I already talked about the issues with bid protests in the acquisition chapter. The dashboard is an important part because we need to bring all the data together to have a more holistic picture of the risk the organization is facing. For example, if you are patching things really well but your signatures on your endpoint virus protection are out of date, that will lead to one risk profile. If your virus signatures are out of date and you have data that isn’t flowing through a Trusted Internet Connection (TIC) then that is a different risk profile. My take on phase 3 is that it is trying to ensure that we are devoting resources to the most important things that will impact the actual risk to the agency.
Remember, the only thing any of us has on this world is time. Where are we going to invest our effort? CDM is a tool that helps us to ensure that we are pushing that effort to the most important things. This is critical because there is a shortage of skilled cybersecurity people. We don’t have enough of them and this isn’t a problem that can be solved with money. We couldn’t simply award more contracts to get those skilled people, because there aren’t enough of them. As such it is important that we spend this effort as wisely as possible. Don’t have these people work on inconsequential dumb shit.
So we need to figure out how to get new, innovative, and some disruptive companies onto CDM so that we can have some real competition, not just on price, but more importantly, on different methods for securing agencies. But after that, we need to ask, what is next? What do we want CDM to continue to evolve into? Clearly I would advocate for a move that supports source code scanning, but that is a straightforward commodity play. Easy.

