A new survey from Tripwire, a security and compliance automation software provider, found that organizations need to go back to basics and make sure they are properly implementing and maintaining cybersecurity fundamentals. The survey, released today, found that organizations are not focusing on basic security controls that the Center for Internet Security (CIS) refers to as “cyber hygiene.”
CIS has a list of 20 “controls” that it considers to be established cybersecurity best practices, and says that by following the top six controls, organizations can establish good cyber hygiene.
The six controls needed to achieve cyber hygiene are inventory and control of hardware assets; inventory and control of software assets; continuous vulnerability management; controlled use of administrative privileges; secure configuration for hardware and software on mobile devices, laptops, workstations, and servers; and maintenance, monitoring, and analysis of audit logs.
Tripwire, in partnership with Dimensional Research, examined how organizations are implementing the security controls needed to achieve cyber hygiene. To develop the report, Tripwire surveyed 306 participants in July 2018, all of whom are responsible for IT security at companies with more than 100 employees.
Implementing Industry Standards
Troublingly, the survey found that the majority of organizations–60 percent–do not use hardening benchmarks, such as CIS or Defense Information Systems Agency guidelines, to establish a secure baseline. “While many security teams implement good basic protections around administrative privileges, these low-hanging-fruit controls should be in place at more organizations,” the report says.
“These industry standards are one way to leverage the broader community, which is important with the resource constraints that most organizations experience,” said Tim Erlin, vice president of product management and strategy at Tripwire. “It’s surprising that so many respondents aren’t using established frameworks to provide a baseline for measuring their security posture. It’s vital to get a clear picture of where you are so that you can plan a path forward.”
Improving Visibility
The report also found that organizations lack visibility into their environments and struggle to quickly address potential security issues. While cyberattacks can happen quickly, 57 percent of respondents noted that it takes hours, weeks, months, or even longer to detect new devices connecting to their network. However, on a positive note, organizations are improving their detection speed when compared to responses to a 2015 survey.
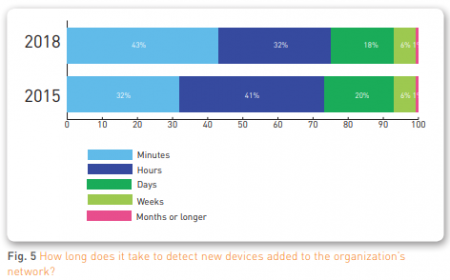
“While tracking each and every device is challenging in dynamic environments, a small percentage of untracked devices could be a significant chunk of the attack surface in a large organization,” the report cautioned.
Detecting and Patching Vulnerabilities
The study found that the vast majority (89 percent) of respondents are running vulnerability scans. However, the frequency of the vulnerability scans leaves something to be desired.
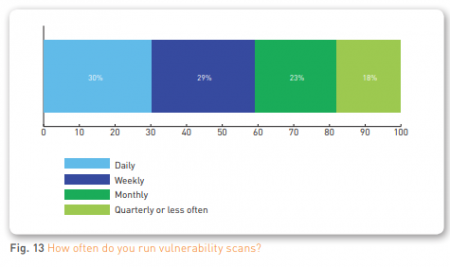
Less than a third of organizations are running daily vulnerability scans and only slightly more than half of organizations (59 percent) are running daily or weekly scans. On top of that, only 50 percent of organizations running vulnerability scans are running the more comprehensive authenticated scans.
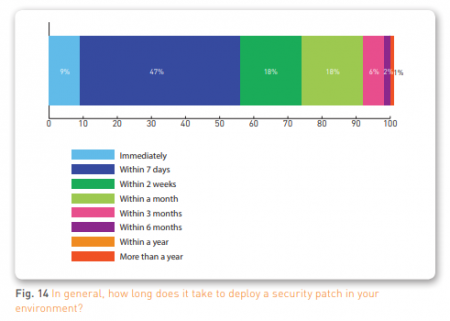
When it comes to deploying security patches, there is a wide range of timetables. While half of organizations get a patch deployed in a week or less, about a quarter of organizations take a month or longer to deploy a patch.
Strengthening Passwords
When given a choice, the average user will choose a weak password. Despite countless high-profile news stories extolling the importance of strong passwords, “123456,” “password,” and “qwerty” still remain popular. To maintain strong passwords, organizations need tough requirements and they need to require frequent password changes. However, organizations aren’t enforcing industry best practices. The survey found that 31 percent of organizations do not require the default password to be changed and almost half (41 percent) don’t use multifactor authentication for accessing administrative accounts.
“Administrative credentials are as valuable as the data you’re trying to protect,” the report explained. “Organizations should provide the same level of care with them as with their most sensitive data.”
“When cyberattacks make the news, it can be tempting to think a new shiny tool is needed to protect your environment against those threats, but that’s often not the case,” said Erlin. “Many of the most impactful and widespread cybersecurity issues stem from a lack of getting the basics right. Cyber hygiene provides the foundational breadth necessary to manage risk in a changing landscape, and it should be the highest priority cybersecurity investment.”

