
The House Oversight and Government Reform Committee’s information technology and government operations subcommittees held a joint hearing Wednesday to key in on the most salient, persistent, and omnipresent issue in Federal agency IT: cybersecurity. On hand to testify were Federal CIO Suzette Kent, and Comptroller General Gene Dodaro, seeking to illuminate congressional inquirers on Federal agency progress to mitigate the wide range of cyber risks.
The hearing yielded a new Government Accountability Office (GAO) interim report on critical actions needed and an update from Kent on the Federal government’s progress on IT Modernization goals. Participants breezed through several of the most pressing areas of interest: critical infrastructure (CI), government-wide strategy, enabling legislation, and workforce gaps.
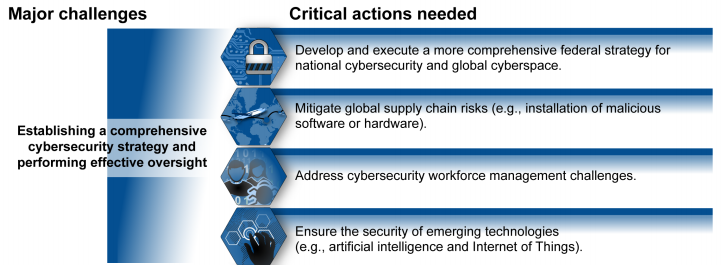
“We at GAO designated cybersecurity across the Federal government as a high-risk area in 1997, so nobody can say we didn’t warn people that this was going to be a problem,” said Dodaro. Acknowledging how that pervasive problem has evolved over time, Dodaro and Kent were tasked with mapping actions to combat it in the future.
Critical Infrastructure
After designating information security as a high-risk area for the Federal government in 1997, GAO added the protection of CI to its high-risk list in 2003. Robin Kelly, D-Ill., the ranking member of the IT subcommittee, looked to Wednesday’s GAO report for an update on progress in that area and returned with concerning conclusions about the current situation.
“GAO found that the Trump Administration’s plans failed to include basic components needed to carry out a national strategy for protecting critical cyber infrastructure,” she said, adding that the plan did not identify key milestones to gauge progress or identify resources needed to carry out goals.
Dodaro, the head of GAO, responded by keying in on an aspect of the CI debate that continues to drive a wedge between coordinated efforts across government and the private sector.
Since many providers of the services categorized under the 16 CI sectors–such as utilities, financial markets and telecommunications–come from private industry, government’s ability to ensure appropriate cyber actions by these companies is limited in scope, Dodaro said.
“By and large critical infrastructure protection is a voluntary effort by the private sector,” he said. “So, there’s really not a clear picture, in my opinion, across the [sixteen different CI] sectors.”
Top-Down Strategy
Many of the subcommittee members expressed a need for an overarching Federal strategy to tackle cybersecurity risks–the first major challenge highlighted in the new GAO report. Dodaro said that a coordinated strategy “needs to be led out of the White House,” adding that coordination “needs to happen at all levels but somebody needs to be in charge.”
Kent addressed exactly how the White House’s Office of Management and Budget (OMB) is charged in the cyber fight. “Our roles align to three main things: development of policy and oversight for the Federal civilian systems, assisting agencies with data analysis and budget, and gathering evidence that promotes solutions that achieve these policies and standards,” she said.
While she stressed the onus on individual agencies for protection of their own cyber infrastructure and the overarching authority of the Department of Homeland Security to coordinate efforts, she said that OMB is working with DHS, the Defense Department, the intelligence community, and the inspector general community to “address both the agency-specific and enterprise demands.”
Legislation
Legislation seeking to modernize and secure Federal agencies also factored prominently Wednesday, and two of the biggest congressional proponents had their say. Rep. Will Hurd, R-Texas, called the Modernizing Government Technology (MGT) Act essential to breaking a cycle of a “if you don’t use it you lose it” in Federal agencies.
Hurd, here alluding to modernization funding, found an ally in Kent. The vehicle Congress proposed to break that cycle is the Technology Modernization Fund (TMF) authorized by MGT. Kent sits on the TMF Board, and with funding in question for next year, urged its renewal.
Rep. Gerry Connolly, D-Va., thanked Dodaro for GAO’s continuous help with the evolving FITARA scorecard, which recently added an MGT category. Hurd questioned both Dodaro and Kent on why so many agencies have struggled on the MEGABYTE Act, an aspect of the FITARA scorecard that requires an inventory of their active software licenses.
Dodaro and Kent conceded that it was not a difficult goal to accomplish, and Kent noted that tools to create these inventories are readily available. She also thanked Hurd for the focus on the FITARA scorecard. “Having that level of transparency does make it a priority,” she said.
Hurd pressed further on what can be done to round out lagging agencies. “What other carrots, sticks should we be using, or do you need, in order to compel compliance on some very basic things like knowing what software you have?” he asked. Kent said basic functions is perhaps hindered by an issue that has become a newly-highlighted administration priority.
Cyber Workforce
“One of the things that I would ask that would be of great assistance is the continued focus on workforce activities,” Kent said. “In many cases we still have almost a 25 percent gap in the number of cybersecurity resources that we need across Federal agencies.”
She said strong gaps remain in leadership. “Places where we have positions that are key leaders, in many cases, the individuals, when we get them in, their tenure is less than 12 to 18 months,” she said.
Hurd called out the lack of “common job descriptions across the Federal government” and Kent responded that “good progress” is being made “at clarifying the specific positions as well as common nomenclature.” The hearing also keyed in on a GAO report from last month that found most CFO Act agencies aren’t properly classifying cybersecurity workers.
Rep. Paul Mitchell, R-Mich., asked Kent what are the primary drivers of lagging cyber workforce numbers in the Federal government.
“Cyber security professionals have an expectation of quick mobility, large challenges, and some ability to move very quickly in their profession. And some of those things don’t align well [with the Federal government],” Kent said, noting the alarming demand for cyber skills and competition with private sector organizations.
“We’ve got big challenges, I can guarantee that,” Mitchell said.
