
Update: It was announced Friday that the Naval Academy took first place, the U.S. Military Academy took second, and the Royal Military College of Canada took third.
COLUMBIA, Md. –A group of Delaware National Guard officers crowd around a computer as code flashes down the screen. One of them thinks he found a back door that will enable him to access the administrator credentials to the Naval Academy’s networks. Once they have the credentials, they can access the school’s “token,” a piece of classified information that the academy has been assigned to protect.
Once the Red Cell from Delaware breaks into the Naval Academy’s network, they will try to perform the same operation on the U.S. Military Academy, the Coast Guard Academy, the Merchant Marine Academy, the Air Force Academy, and the Royal Military College of Canada, which are all participating in the National Security Agency’s Cyber Defense Exercise.
“It’s very time consuming so it forces us to do things differently than how we normally do them,” said Ryan Sarrol of the Red Cell from Delaware.
It takes the team an average of four hours to successfully carry out an attack on one of the academies. In a real life military situation, Sarrol’s team would spend time researching and developing their attack methods before they carry out a cyber mission. During the cyber exercise, the Red Cell tests as they go.
In order to ensure that the Red Cell doesn’t destroy the academy’s servers by accident, the Red Cell will test the attack on their own networks first. Sarrol had left to get some sleep at 2 a.m. the night before. It’s 11:30 a.m. and he’s back and ready to challenge the Naval Academy.
Blue Cell:

The cyber exercise, which is in its 17th year, hosted students from each of the military academies. The teams from each academy make up the blue cell, and they are responsible for building their own networks and defending them from cyber threats during the week long exercise.
“The whole goal of [the Cyber Defense Exercise] is to help prepare cyber leaders for tomorrow,” said Shirley McMonigle, program manager for the cyber exercise. “We give them the opportunity to showcase their skills.”
The students who participate in the cyber exercise might not immediately join the NSA when they graduate because of their military deployments. But sometimes the students’ assignments change and their experience in the competition makes them solid candidates for a cyber-focused job, according to McMonigle.

The Royal Military College of Canada fields two teams. One undergraduate team competes for the trophy. The other team, a graduate team, doesn’t compete but participates in extra exercises such as a space cyber challenge and defending an unmanned ground vehicle.
“They ran one smack into a wall yesterday because they’re operating it from Canada,” said Jim Titcomb, technical lead for the cyber exercise.
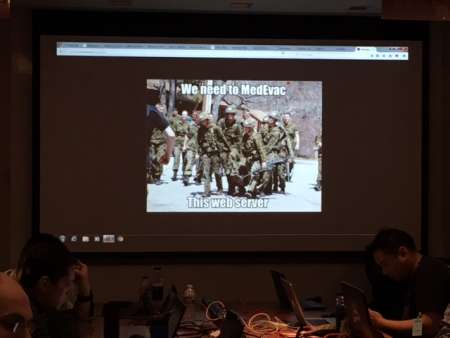
The Canadian team also defaced one of the academy’s websites the night before. Now the home page hosts a picture of struggling military officers with the line, “We need to MedEvac this web server.”
The students prove their skills in the form of malware detection and analysis, network forensics, offensive ethical hacking, and carrying out missions with virtual military drones. The students gain points by protecting their “token” from being stolen or tampered with, securing their networks, and keeping their networks up and running for users.
“We don’t pick on one individual school,” said Titcomb. “Everything that is done is done to every academy.”
White Cell:
The White Cell includes members of the NSA who serve as referees for the competition. Because the students can’t attack the servers setup by other teams, the White Cell investigates each team for misconduct.
As of Wednesday morning, the White Cell had convicted one team of going outside of the directive. The Coast Guard Academy had been able to rig the system so that they could ping another academy’s server even though the network was down at the time. The team lost points for the misconduct.
Gray Cell:
The Gray Cell is a combination of automated systems and humans that act as the average user of a network, able to receive emails and surf the web.
“We call it the user that clicks on everything,” Titcomb said.

The gray cell could click on a link that directs them to a phishing attack, just like the average user in a real network.
“It allows [the students] to see firsthand, what happens in the real world,” Titcomb said.
Michael Rau, Gray Cell lead, said that the user doesn’t always act maliciously.
“We can act in an ignorant manner or actually pass back information about the network to adversaries,” said Rau.
Red Cell:
The Red Cell includes members of the NSA, the Canadian Forces, the Swiss Red Team, the Delaware National Guard, and commercial red teams.

For the first year, the Red Team is also hosting students from the academies to teach them offensive tactics.
“It’s been a lot of watching and learning,” said Conner Eckert, a 20-year-old cadet at the Military Academy.
Eckert said that most of his experience had been in defending networks and he hopes that his classmates can aspire to bring themselves to the level of the professional red cell members.
Another new feature this year is a ransomware attack that will be injected into the academies’ systems on Wednesday. The students will have to decide whether to pay 3,000 points to get back their encrypted information or hack their way out of the ransomware.
“If they reboot their system, it’s gone,” said Titcomb. “It acts like real ransomware.”
The Red Cell uses attack methods that are simple and open sourced.
“Simple things that would be caught by an undergraduate student is what we throw,” Titcomb said. “We don’t let them know what we use and how we get it.
One year an academy wrote their passwords on a white board that was within view of the video cameras that monitor each team. The Red Cell was able to use these to gain administrative access to the network.
However, this year the scores are all relatively high. On Tuesday night, three of the networks were compromised but each team was able to defend its systems and push the Red Cell out.
After a fierce day of competition, @WestPoint_USMA takes the #1 spot in our #CDX leader’s scoreboard. Visit @NSAGov for daily #CDX coverage. pic.twitter.com/w8Z7aPO9jT
— NSA/CSS (@NSAGov) April 12, 2017
